Ever wondered how Windows Authentication work?
Table of Contents
Windows Authentication
If you ever used Windows, you might have seen following login screen a number of times. Have you ever wondered how login actually works on Windows? In this series of blog posts, let’s deep dive into Windows login. Let’s start with the types of logons.
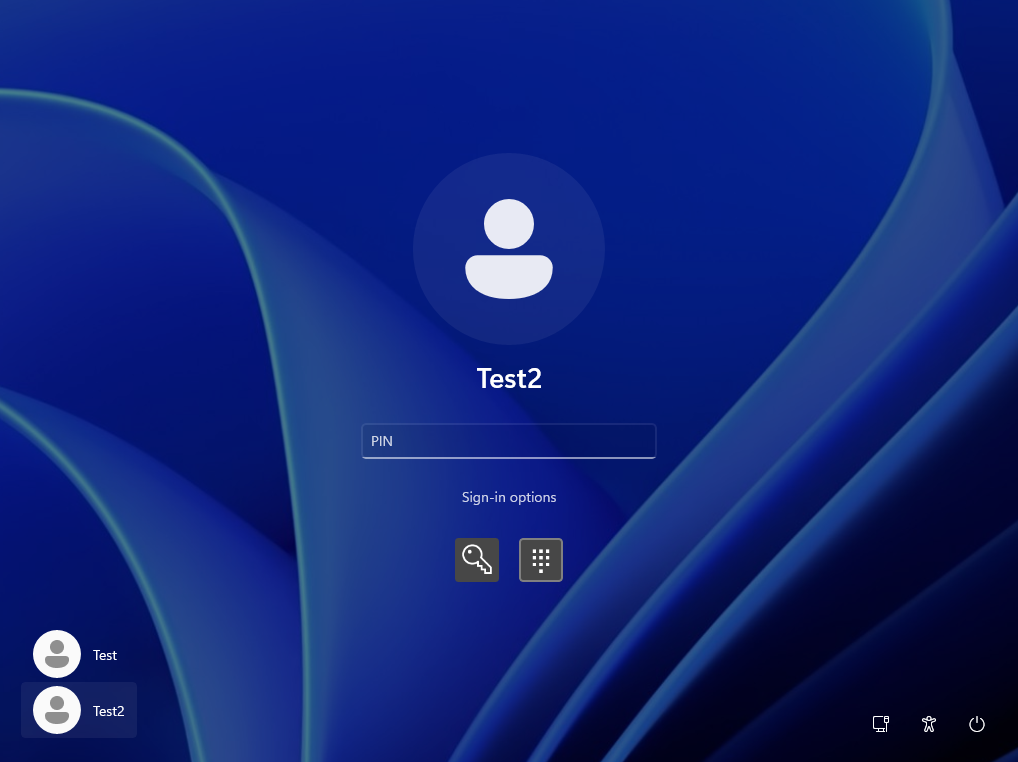
1. Local Logon
In the early days of Windows, specifically during the late ’80s and early ’90s, the concept of domains or the Internet did not exist. Each machine operated in isolation, and users logged in locally.
- Mechanism: When you log in locally, your credentials (username and password) are validated by the local machine.
- Scope: This type of logon is limited to accessing resources on the specific machine where the logon was performed.
- Common Use: This is still common in workgroup environments where there is no central authentication authority.
2. Microsoft Account Logon
With the advent of Windows 8, Microsoft introduced the ability to log in using a Microsoft account (previously known as Windows Live account).
- Mechanism: This type of logon uses Microsoft’s cloud services to authenticate the user.
- Scope: It allows users to access their personal settings and files across multiple devices by synchronizing with their Microsoft account.
- Common Use: Ideal for personal devices where users want a seamless experience across their Windows devices.
3. Domain Joined Logon
For enterprise environments, domain logons have been a cornerstone since the introduction of Active Directory.
- Mechanism: Users authenticate against an Active Directory (AD) service using protocols like Kerberos and NTLM.
- Scope: This type of logon allows users to access resources across the entire corporate network, provided they have the necessary permissions.
- Common Use: Widely used in businesses and organizations for managing user access to network resources.
4. Azure AD Logon
As businesses move towards cloud-based solutions, Azure Active Directory (Azure AD) has become prevalent.
- Mechanism: Similar to domain logons, but the authentication is handled by Azure AD, Microsoft’s cloud-based identity and access management service.
- Scope: Allows access to cloud-based applications and resources, facilitating single sign-on (SSO) across various services.
- Common Use: Used by organizations that have adopted Microsoft 365 or other Azure services.
5. Hybrid Domain Logon
To bridge the gap between on-premises and cloud-based resources, hybrid domain join solutions are implemented.
- Mechanism: Users authenticate against both on-premises Active Directory and Azure AD. This dual-authentication mechanism supports seamless access to both on-prem and cloud resources.
- Scope: Facilitates single sign-on (SSO) and provides a unified experience across different environments.
- Common Use: Ideal for enterprises transitioning to the cloud while maintaining their on-premises infrastructure.
Credential Providers and Their Roles
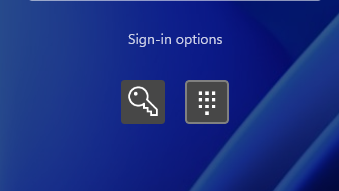
The Sign-in options listed in the image above are based on the available Credential Providers on the machine. Credential providers play a vital role in the Windows logon process. They collect and validate user credentials and hand them off to the appropriate authentication service. Following are most common credential providers:
- Password: The most common credential, where users input their username and password.
- Windows Hello: Uses biometric data such as facial recognition or fingerprints and PIN. These credentials are stored locally and never leave the device, ensuring a higher level of security.
- FIDO (Fast Identity Online): Utilizes physical devices like security keys, which provide a secure, hardware-based authentication method.
- Smart Cards: Physical cards that store user credentials, providing an additional layer of security.
Next, let’s take a look at the process that shows logon UI to the user. The process is aptly named as LogonUI.exe
LogonUI.exe
LogonUI is the user interface process that presents the logon screen when you start your Windows machine. This interface is responsible for collecting the user’s credentials, such as passwords, PINs, biometrics (fingerprints, facial recognition), and smart cards, and then passing them to the appropriate system components for authentication.
How LogonUI Works
- Presentation of Credential Providers:
- When you boot up your Windows machine,
LogonUIdisplays the logon screen. This screen includes various credential providers. Credential providers are specialized plugins that collect different types of credentials (e.g., passwords, PINs, biometric data). - The logon screen allows you to enter your credentials. It could be a password, a PIN, or biometric data like a fingerprint or facial recognition.
- When you boot up your Windows machine,
- Handling Credentials:
- Once the user enters their credentials,
LogonUIcaptures this information and sends it to theWinlogonprocess.Winlogonmanages the overall logon experience and interacts with the local security authority subsystem service (lsass).
- Once the user enters their credentials,
- Interaction with Winlogon and Lsass:
Winlogonreceives the credentials fromLogonUIand forwards them tolsassthrough an API calledLSAlogonUser.lsassis responsible for the actual authentication process. It verifies the credentials against the stored user data using various authentication packages (like Kerberos, NTLM, OAuth).
- Authentication Packages:
- These packages represent different protocols that handle the authentication of the provided credentials. For instance, Kerberos and NTLM are common in enterprise environments for validating user identities.
- Post-Authentication Actions:
- After successful authentication,
lsassnotifiesWinlogon, which then proceeds to initialize the user session. This involves loading the user profile, starting the desktop environment, and running any login scripts if necessary.
- After successful authentication,
- Creating the Desktop:
Winlogoncreates the user desktop by loading the necessary components such as the registry settings, user-specific configurations, and any network resources.- It also starts
Userinit, which executes logon scripts and finally startsExplorer, the Windows shell that provides the desktop, taskbar, and Start menu.
Detailed Flow of Events
- User Initiates Logon:
- The user sees the LogonUI interface upon system start.
- The interface includes various options depending on the configured credential providers (password, PIN, smart card, biometrics).
- Credential Entry:
- The user enters their credentials.
LogonUIcaptures this input with the help of credential providers and forwards it toWinlogon.
- Processing Credentials:
Winlogonpasses the credentials tolsassviaLSAlogonUser.lsassuses the appropriate authentication package to validate the credentials.
- Authentication Confirmation:
lsassconfirms the credentials and informsWinlogonof the successful authentication.Winlogonstarts the process of creating the user’s desktop environment.
- Loading User Profile:
- Winlogon loads the user profile by accessing the registry, user-specific settings, and any network resources.
Userinitruns any necessary logon scripts specified in Active Directory.
- Starting Explorer:
- Finally,
Userinitstarts the Explorer process, which provides the user interface elements like the Start menu and taskbar. - The user is now logged in and can interact with the Windows desktop environment.
- Finally,
Local Security Authority (LSA)
The Local Security Authority (LSA) is a critical component in the Windows operating system, responsible for managing security policies, auditing, and handling authentication. One of its key roles involves working with authentication packages, such as the Negotiate package, to verify user credentials and facilitate secure logons.
LSA itself doesn’t directly process passwords or authentication requests. Instead, it hosts various services that handle these tasks. This design allows LSA to support different security functions, including:
Authentication: Verifying user credentials through various authentication packages.
Auditing: Monitoring and logging security events.
Secret Management: Protecting cryptographic keys and other sensitive information.
Authentication Packages
Authentication in Windows is handled by a system of Auth Packages, each representing a different protocol for verifying user identity. Common examples include:
Kerberos: A network authentication protocol designed to provide strong authentication for client-server applications.
NTLM: A suite of Microsoft security protocols that provides authentication, integrity, and confidentiality to users.
OAuth: An open standard for access delegation commonly used for token-based authentication.
When a user attempts to log on, LSA interacts with these packages to determine which protocol to use for validating the credentials. Credential Providers gather credentials from the user (such as a password or smart card) and submit them to LSA. They specify which Auth Package should be used for the logon process. For instance, when a user types in their password, the Credential Provider might direct LSA to use the Negotiate package.
Negotiate Authentication Package
Negotiate is a special Auth Package in Windows that simplifies the process of choosing an authentication protocol. Here’s how it works:
Credential Submission: The Credential Provider submits the user’s credentials to LSA and indicates that the Negotiate package should be used.
Protocol Selection: Negotiate examines the available Auth Packages to determine which one can handle the credentials. It follows a predefined order of preference, typically starting with Kerberos and falling back to NTLM if necessary.
Cached Logon: If the user is logging on without network access, Negotiate may use the NTLM cached logon mechanism. This allows the user to access the desktop using previously cached credentials, ensuring quick logon even when offline.
Detailed Flow of Negotiate Package
- The process begins when the user enters their password at the login screen.
- The Credential Provider indicates that the Negotiate package should be used and passes the credentials to LSA.
- Negotiate calls the LsaLogonUser function, initiating the logon process.
- Auth Package Routing: LSA routes the request through the available Auth Packages:
- NegoEx: This package handles specific protocols for single sign-on scenarios but might not be used for standard logons.
- Kerberos: If the credentials can be verified via Kerberos, this package communicates with the domain controller to authenticate the user.
- NTLM: If Kerberos is unavailable (e.g., the machine is offline), NTLM can perform a cached logon using stored credentials.
- Cached Logon with NTLM: If NTLM is used, it verifies the user’s credentials against the cache and allows access to the desktop.
Online and Offline Logon
Negotiate can handle both online and offline logons:
Online Logon: When the machine is connected to the network, Negotiate may use Kerberos to contact the domain controller and authenticate the user.
Offline Logon: When offline, NTLM performs a cached logon, using previously stored credentials to quickly grant access.
To let the user logon immediately, some of the processing happens in the background after user logs in. lsass will kick off a background thread and perform Negotiate again with available network protocol like Kerberos.
Key Points
Efficiency: The Negotiate package ensures efficient logon by quickly determining the best available Auth Package to handle the credentials.
Security: By routing through different Auth Packages, Negotiate maintains a high level of security, leveraging protocols like Kerberos and NTLM.
Flexibility: The ability to handle both online and offline logons makes Negotiate a versatile solution for various logon scenarios.
Upcoming blog
In the next post, we will go deeper into each of the protocols used for logon starting with Kerberos.
Exercise
In interesting exercise for a security student/professtional would be to threat model Windows authentication process. If you are not familiar with how to threat model, definitely take a look at Thread Model 101.
Resources
Windows Authentication Overview | Microsoft Learn
Credentials Processes in Windows Authentication | Microsoft Learn
Winlogon and Credential Providers – Win32 apps | Microsoft Learn
